- Home
- Articles
- Why do you need a comprehensive Security Management Program?
7/08/2019
Why do you need a comprehensive Security Management Program?
Before we address the question, it helps to provide context.
Undertaking the work to put together a Security Management Program requires planning. It is a project in its own right and requires the time and commitment from a number of individuals to do well. Any dilution or shortcutting will result in token and often ineffective solutions. One of the challenges many security directors and managers have to deal with, is a lack of understanding about what security risk is.
A well-constructed Security Management Program and broad awareness of content will resolve the risk knowledge gap. Your program should be aligned alongside and within the internal control framework adopted by the Board of Directors as part of their corporate governance responsibilities.
Good risk management is difficult to implement, and failing to grasp that single fact may explain why many organizations, that take risk every day, get the management of risk wrong. There seven core reasons why this is the case are:
- The potential interaction of multiple risks was underestimated or disregarded
- Probabilistic modelling was over-emphasized; shortcuts were taken; scenario planning was underused; transparency into potential issues was absent
- Risk managers were isolated in silos
- Warnings were ignored; those who delivered them were dismissed as negative or criticized for not being team players
- A short-term perspective with a single-minded focus on making the quarterly financials
- Companies lacked a comprehensive approach to firm wide risk management; authority and responsibility were poorly controlled and defined
- Risk management often focused on compliance rather than performance, leading to inadequate assessments and responses
There are also misunderstandings regarding the distinction between security management plans and programs. It might seem like a transferable terminology but it is not. There are many references to security management plans when in actual fact the requirement in almost all circumstances is for a security management program. Plans are documented and sit on the shelf – only to be looked at in an emergency situation. Programs, on the other hand, are viewed regularly. They are always being practiced and tested.
- Plans are based on theory; Programs are based on results
- Plans are dormant; Programs are active
- Plans become obsolete; Programs evolve
Plans also have value and support programs. The plan is the objective and the vision, whereas the program is the content and steps taken to reach the goal.
A properly maintained Security Management Program gives you risk scores that are always current and will properly drive forward planning and all program activities. There should be no doubt why having a Security Management Plan is necessary, why the investment that could be required to implement it should be regarded as a priority, and why it should be included as part of the risk management framework used by an organization and monitored in an ongoing process, on an ongoing basis.
Your comprehensive Security Management Program will be the product of four comprehensive phases:
- Strategy and Planning– introduces a number of Business Management Concepts (BMC’s) that will help any organization position its Security Management Program within their environment to ensure its successful implementation. By identifying these (BMC’s) beforehand, the process of raising awareness and securing buy-in to the Security Management Program at the right time, will happen as and when you, the as the party responsible for security, need it. The Security Management Program will have visibility and acceptance within the organization and have a greater chance of implementation
- Assessment –It will be evident that the Risk Assessment process is quite detailed and will in most cases take a reasonable amount of time to conduct. However, once completed this will provide a thorough understanding of risks facing your organization, and also an excellent basis upon which to formulate the remainder of the Security Management Program. It will also provide a key tool for ongoing risk management activity in the form of the Risk Register, which can be updated on a regular basis to ensure that your organization is always in control of the risks facing the company and its assets.
- Design – Infrastructure security design is a very complex area and despite any person being able to obtain a broad overview of the subject matter, it is likely that the level of technical expertise necessary to design your Integrated Security Solution will only be available from external specialists in this field. It is important to ensure that where necessary external support is made available to the Project Team since the potential for cost overrun associated with a poorly designed project far outweighs the small initial cost of independent design consultancy. By connecting to external specialists, you will gain access to a sequential process that allows you to design and specify the most important aspects of a robust risk mitigation solution – those that relate to its performance. Subsequently, this will form the basis for engagement with your external providers in a controlled manner, providing reassurance to stakeholders that business risks will be mitigated in a cost-effective manner.
- Implementation & Monitoring –This final phase of the formation of a Security Management Program completes the development cycle towards the management of risk for your organization in a cost-effective, quality-assured manner. Future Program-related activities are then ensuring the program is maintained and sustained. The whole risk management program and process from implementation forward must be open to an audit process that ensures that a) the program and process has been implemented as well as it should be, and b) remains current and reflective of the dynamic environment it seeks to operate within.
There is no doubt that the trend in risk management – irrespective of which risk – is towards greater maturity. One of the first steps is to establish the organization’s current maturity level, before incorporating maturity improvement in your security management plan.
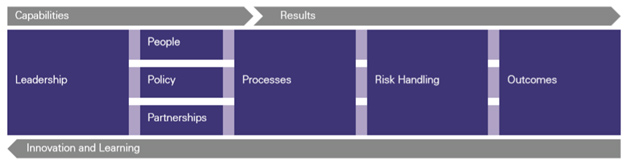
That maturity level is the outcome of seven core questions under 3 categories.
Capabilities:
- Do senior management support and promote risk management?
- Are people equipped and supported to manage risk well?
- Is there a clear risk strategy and risk policies?
- Are there effective arrangements for managing risks with partners?
- Do the organization’s processes incorporate effective risk management?
Risk Handling:
- Are risks handled well?
Outcomes:
- Does risk management contribute to achieving outcomes as noted above?
The maturity levels between 1 and 5 on a rising sliding scale are:

The operating environment in all sectors is becoming more complex and requires the best possible risk management to be evident in an organization in order to satisfy the risk to reward expectations of an increasingly complex and interwoven Stakeholder environment. Advancing your security maturity on the sliding scale your goal.

